How to add SSH Keys in Google Cloud VM Instance
I’ve been here and believe me there is no straight answer for this. If you’re a beginner and recently switched to Google Cloud, then it is nearly impossible to add your own SSH Keys and to get it to work on the first time.
Google Cloud recommends to use Google Cloud Console, which is good but for me, it is an overkill if you know what you are doing. The whole process gets complicated for a simple task. So, without wasting time, I’ll just show you how to add your own SSH Keys in Google Cloud VM Instance.
Add SSH Keys on Google Cloud
There are two ways you can easily add your own SSH Keys to Google Could VM.
- Project-wide Keys
- VM specific Keys
The project-wide keys will be injected into the Virtual Machine in all the running VM instances.
Steps to add your own SSH Keys to Google Cloud (Project-wide)
- Log in to your Google Cloud account.
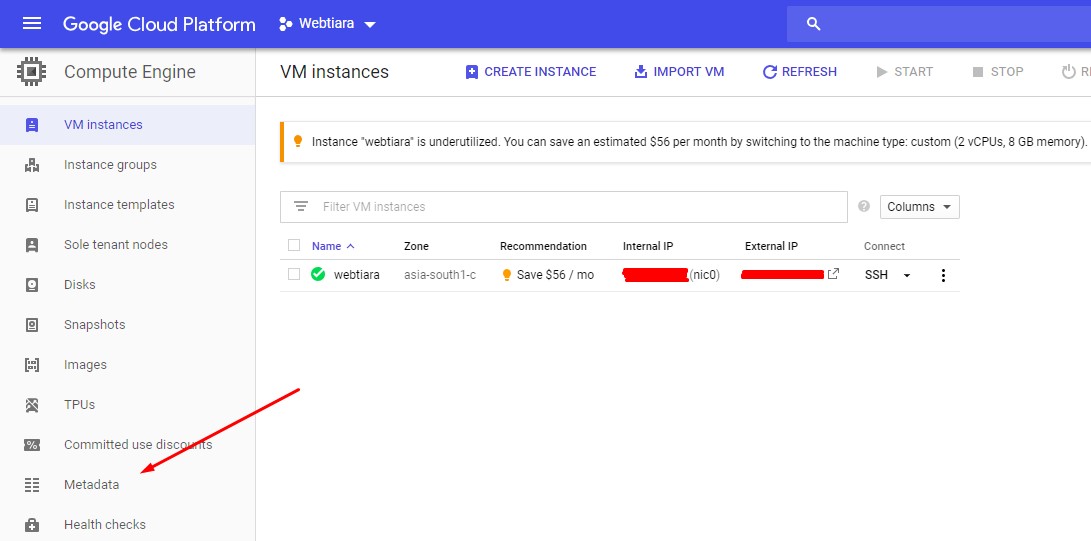
- Navigate to your Compute Engine menu
- And then select Metadata submenu
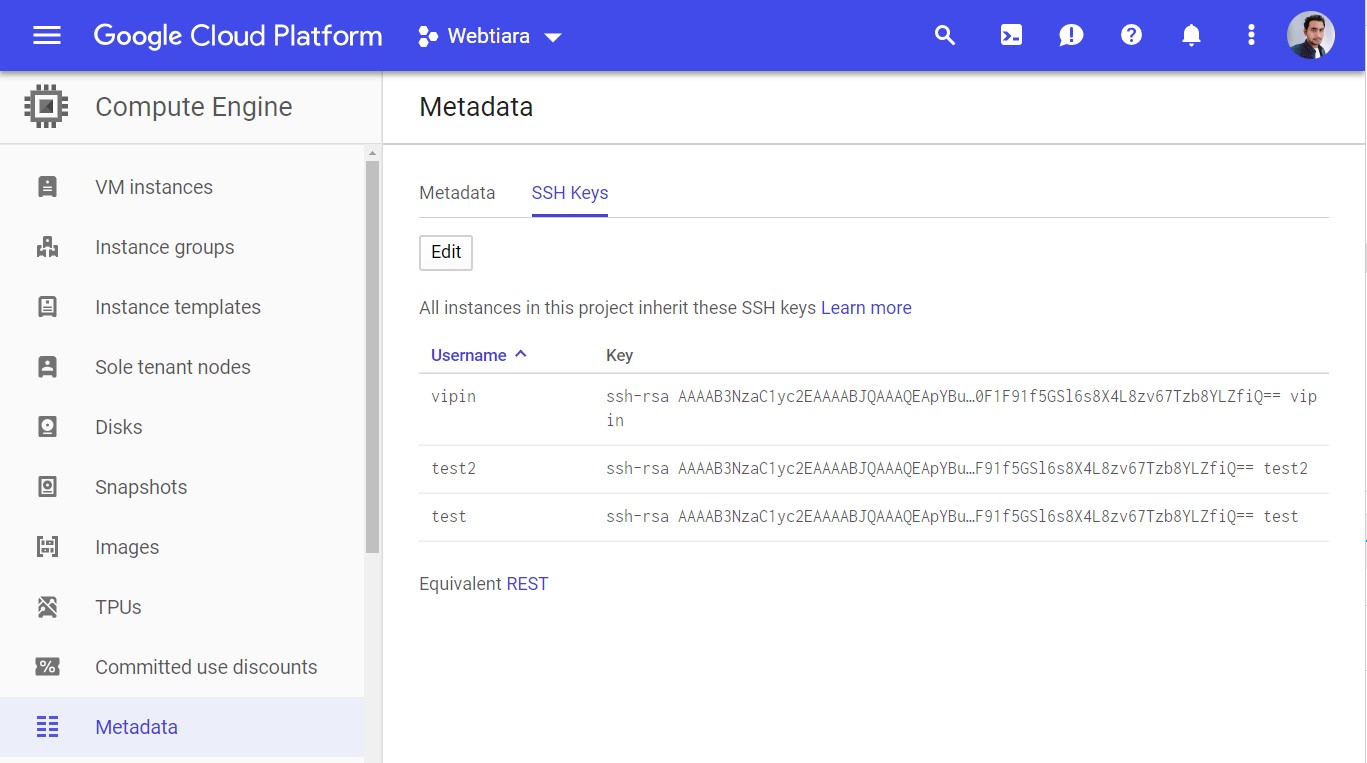
Compute Engine Metadata SSH Keys
Click on the “SSH Keys” tab and click edit to paste your own keys
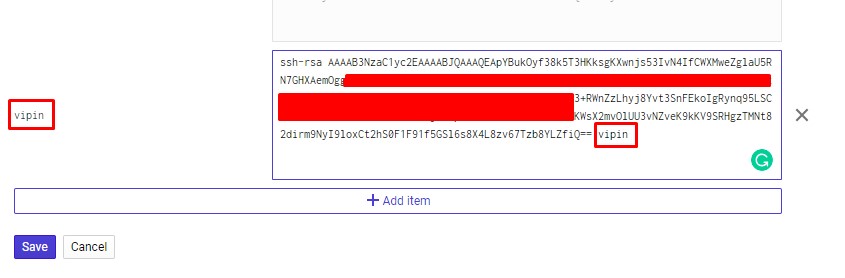
Adding Google Cloud SSH Keys
Steps to add your own SSH Keys on a specific VM on Google Cloud
Click on the VM you want to add your SSH Keys.
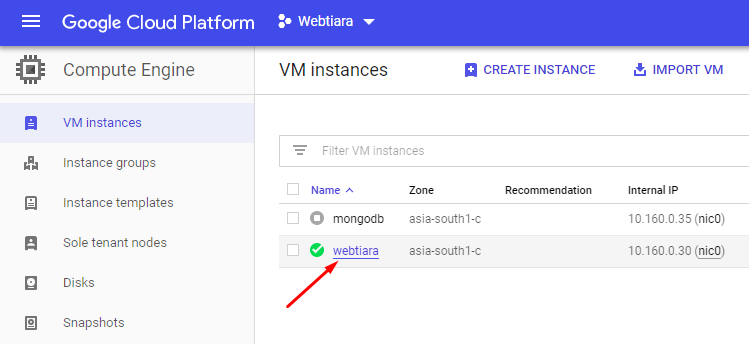
click on vm instance to edit
Click edit at the top to tweak VM settings
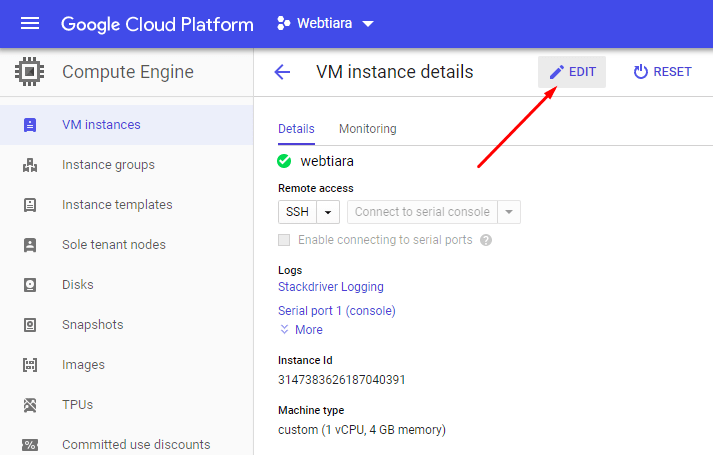
edit google cloud vm
Scroll down to add SSH Keys section and paste your Public Key in the edit box and save
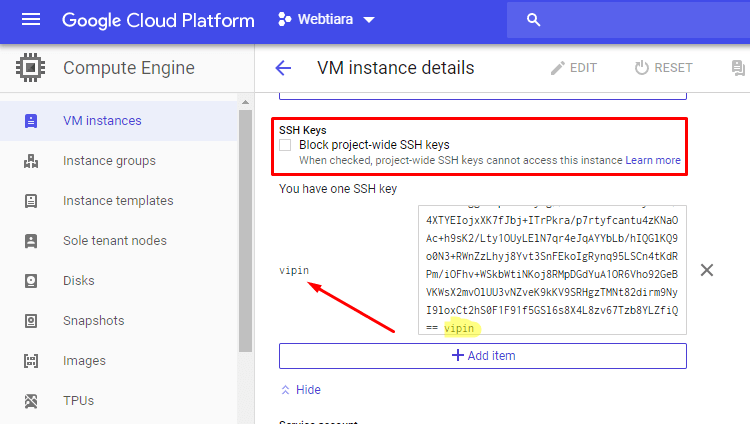
add ssh keys to google cloud vm
Tip: You can also check the “Block project-side SSH Keys” checkbox to prevent injecting the Keys entered in project-wide metadata settings.
So now you’ve installed the Keys properly in the VM. It was simple right? But then why it doesn’t seem to be working? I’ll explain what is happening in the background.
Let’s take the following example.
When you paste/add your own keys. Google creates a new user account in your VM instance.
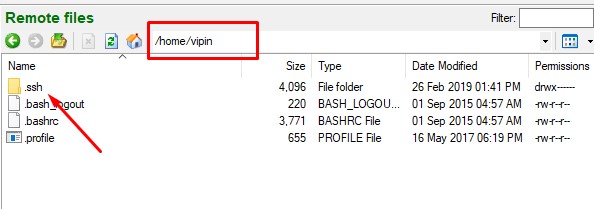
Newly added user with SSH Key
So, when you log in using your SSH client, in my case I’m using Bitvise SSH Client. In the username field enter the exact same user name which was in the SSH public key.
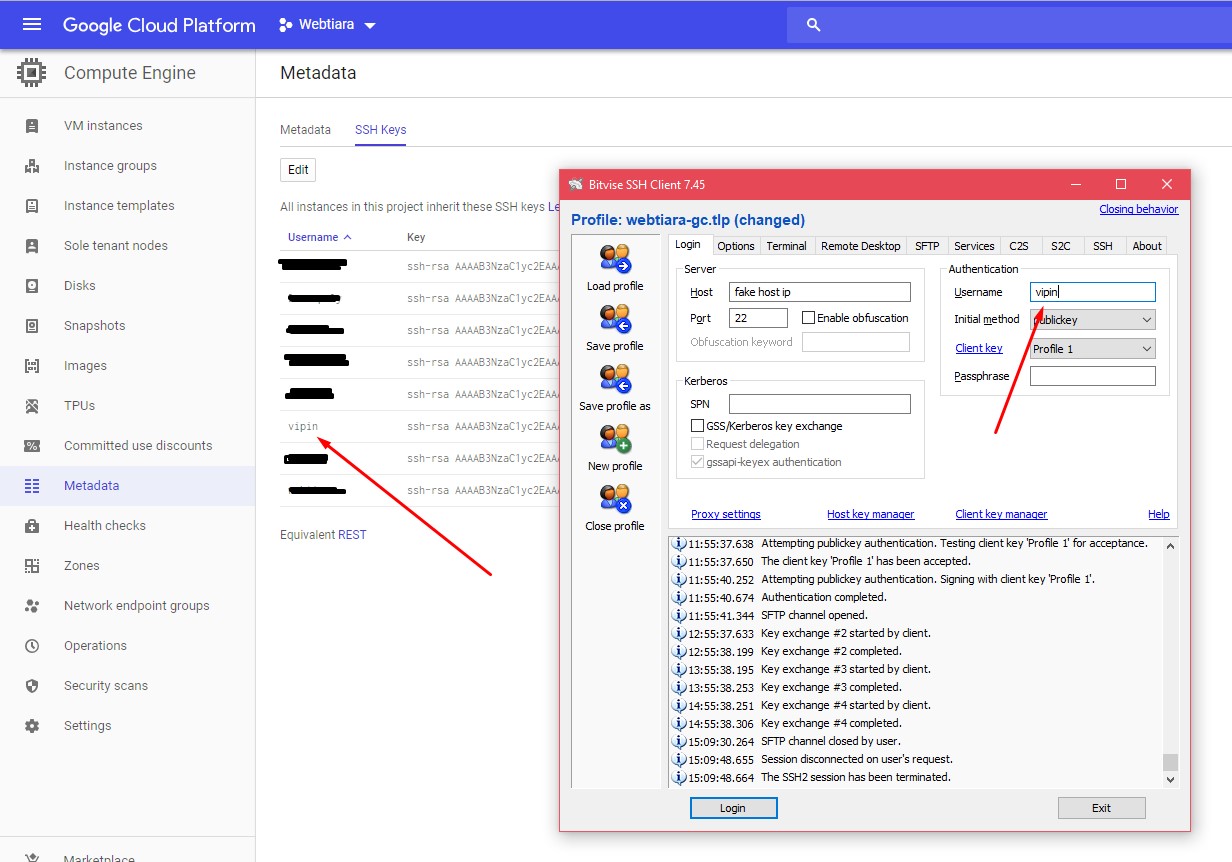
Make sure the user name and the comment in SSH key match
And if you already have a user created in your VM instance then use that username at the end of your public SSH key.
You can definitely add your own keys by editing ./ssh/authorized_keys file in any code editor but it won’t help much as Google Cloud removes all the SSH keys periodically or when you try to access SSH console in the browser to make sure any malicious installed program is not sharing the VM Instance access.
Don’t worry Google Cloud Compute Engine will add only the SSH Keys which are saved in the metadata options.
SSH Authorized Keys
I hope this will help you set up easy access to your Compute Engine VM without too much hassle. If you have any questions then tweet me at @vip_iny, I’ll try to help you with your query.